News
WordPress 5.7.2 version patches for a critical vulnerability

A WordPress vulnerability is having the rating of critical as it has been patched. The exploit has the labeling as critical. However, one of the security researchers states that the critical vulnerability is being exploited as the remote one.
This patch has the application to the WordPress version 5.7.2. Sites have opted into the new automatic download. They should also be receiving this update without any kind of additional action from the publishers.
Publishers are now encouraged to check what WordPress version they are using. They also need to make sure that they are using version 5.7.2.
The vulnerability which is affecting WordPress has the name as an Object Injection vulnerability. However, it is an object injection in the PHPMailer vulnerability. As per the Owasp.org security website, the definition of the PHP Object Injection Vulnerability is much clearer.
PHP Object Injection is an application-level vulnerability that can allow an attacker to perform various malicious attacks. It can also make them opt for the Code Injection, Path Traversal, SQL injection, and the Application Denial of service based on the context.
The critical vulnerability comes up when the user-supplied input is not having the proper sanitization. As PHP allows for object serialization, attackers can pass ad-hoc strings to the vulnerable un-serialized call. Hence it will result in a much arbitrary PHP object injection to the application scope.
The vulnerability is having a rating near the highest level of criticality. On a scale of 1-10 using the CVSS, the vulnerability is having a rating near 9.8. The Patchstack security website also has the publication of the official United States government vulnerability rating.
The solution is to update WordPress to its latest version. The security updates One security issue which affects the WordPress version between 3.7 and 5.7. The solution is again the update to fix the security issues.
The Official United States Government National Vulnerability Database website announces; this problem happens due to fixes for the previous one. WordPress says there is no need to panic about it. Publishers who are using WordPress should check if their installations are the latest or not.
-

 Domains6 years ago
Domains6 years ago8 best domain flipping platforms
-

 Business6 years ago
Business6 years ago8 Best Digital Marketing Books to Read in 2020
-

 How To's6 years ago
How To's6 years agoHow to register for Amazon Affiliate program
-
 How To's6 years ago
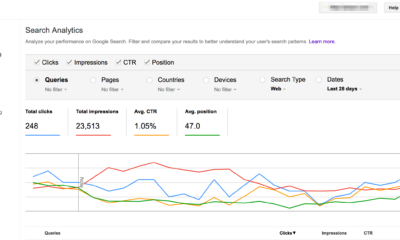
How To's6 years agoHow to submit your website’s sitemap to Google Search Console
-

 Domains5 years ago
Domains5 years agoNew 18 end user domain name sales have taken place
-

 Business6 years ago
Business6 years agoBest Work From Home Business Ideas
-

 How To's6 years ago
How To's6 years ago3 Best Strategies to Increase Your Profits With Google Ads
-

 Domains5 years ago
Domains5 years agoCrypto companies continue their venture to buy domains