News
Google Chrome 84 rolls out restrictive 3rd party cookie handling

We have seen that while Google Chrome has been doing all it can to fix the issue of obnoxious cookie tracking as well as the problems of tracking that their users are complaining about, it is also something that publishers should be concerned about. For example, we have seen that a little change can make websites to not function properly and making changes to cookies will have an impact as well. Now, we are seeing that Google Chrome 84 has been released and the main thing that it comes with it restrictive third party cookie handling.
Now, this is a problem for publishers because some websites that use third party cookies might not be set properly. While this can mean the income is lost for publishers, it could also mean a breakage of website functions which could be an even bigger loss. However, publishers have to keep in mind that third-party cookies that are “served via the insecure HTTP protocol and cookies that do not have the proper SameSite attribute.” will be blocked. This means that if a third party cookie is using the “SameSite=None;Secure” then you are safe.
From the “Secure” tag, the browser knows that cookie is sent via secure protocol which is HTTPS rather than HTTP so the cookie is allowed. Google explains this change in a statement which is as follows:
“One of the cultural properties of the web is that it’s tended to be open by default. This is part of what has made it possible for so many people to create their own content and apps there.
However, this has also brought a number of security and privacy concerns.
Cross-site request forgery (CSRF) attacks rely on the fact that cookies are attached to any request to a given origin, no matter who initiates the request.
For example, if you visit
evil.examplethen it can trigger requests toyour-blog.example, and your browser will happily attach the associated cookies.If your blog isn’t careful with how it validates those requests then
evil.examplecould trigger actions like deleting posts or adding their own content.”
-

 Domains5 years ago
Domains5 years ago8 best domain flipping platforms
-

 Business5 years ago
Business5 years ago8 Best Digital Marketing Books to Read in 2020
-

 How To's6 years ago
How To's6 years agoHow to register for Amazon Affiliate program
-
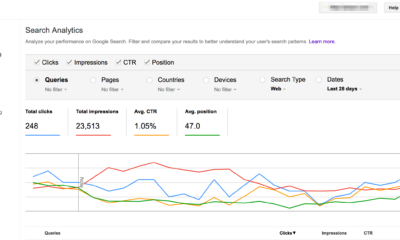
 How To's6 years ago
How To's6 years agoHow to submit your website’s sitemap to Google Search Console
-

 Domains4 years ago
Domains4 years agoNew 18 end user domain name sales have taken place
-

 Business5 years ago
Business5 years agoBest Work From Home Business Ideas
-

 How To's5 years ago
How To's5 years ago3 Best Strategies to Increase Your Profits With Google Ads
-

 Domains4 years ago
Domains4 years agoCrypto companies continue their venture to buy domains