News
WP Super Cache Vulnerability is affecting more than 2 million sites

The discovery of WP super cache vulnerability is a new concern. It is a low severity vulnerability that can allow a hacker to upload and execute some kinds of malicious codes to control the site.
The has finally met its disclosure which is exposing users of WP Super Cache in front of an authentic remote code execution vulnerability. The remote code Execution is an exploit which is allowing an attacker to get the chance from a flaw. This flaw can actually be very advantageous for them to upload and run a few malicious codes.
The common intent is to upload and execute PHP code, which then allows them to do mischievous things. They can install backdoors, access, and make significant changes in the database area to attain administrator-level control on this site.
Once an attacker has administrator-level control, the site can come under his control. According to the glossary published on Wordfence.com, RCE occurs when an attacker becomes able to upload code to your website. A bug in a PHP Application possibly accepts user input and can evaluate it as a PHP code. This can allow an attacker to tell the website to create a new file concealing code that lets the attacker have full access to a website.
When an attacker sends code to a web application, about its execution, with the granting of attacker access, they exploit an RCE vulnerability. This is quite serious. As it is very easy to exploit and grant full access to an attacker after the exploit.
WP Super Cache comes with a variation of RCE exploit, known as Authenticated Remote Code Execution. An Authentic Remote Code Execution vulnerability is an attack where the attacker must have a registration with the site.
The registration level also depends on the exact type of Super Cache vulnerability. Sometimes it needs to be a registered user with editing access. All the attackers need the low registration level as a subscriber level. No details are yet here about which kind of authentication is needed for exploitation.
-

 Domains5 years ago
Domains5 years ago8 best domain flipping platforms
-

 Business5 years ago
Business5 years ago8 Best Digital Marketing Books to Read in 2020
-

 How To's6 years ago
How To's6 years agoHow to register for Amazon Affiliate program
-
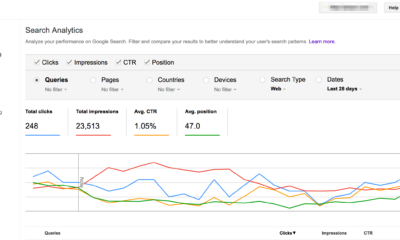
 How To's6 years ago
How To's6 years agoHow to submit your website’s sitemap to Google Search Console
-

 Domains4 years ago
Domains4 years agoNew 18 end user domain name sales have taken place
-

 Business5 years ago
Business5 years agoBest Work From Home Business Ideas
-

 How To's5 years ago
How To's5 years ago3 Best Strategies to Increase Your Profits With Google Ads
-

 Domains4 years ago
Domains4 years agoCrypto companies continue their venture to buy domains