News
Data breach intrusions at 6 more web hosts

While web hosts are trending in big-time nowadays, they have always run the risk of a dreadful data breach. Such breaches can not only put the web hosts at stake but can also tamper with data to invite dire consequences.
In recent days, GoDaddy, one of the most popular web hosts, has fallen victim to a data breach that has affected up to 1.2 million web hosts. This again has expanded itself to 6 more web hosts that serve customers on a worldwide basis. The six web hosts claim to be the resellers of GoDaddy’s hosting services. According to reports, the commencement of the extents of all the intrusions matched the date of all the security intrusions.
The six web hosting providers under attack are 123REG, Domain Factory, Heart Internet, Media Temple, Tso Host, and Host Europe.
The first news of a data breach came out when the state of California released a notification. It was of a security breach in a publication by GoDaddy on November 23, 2021. While the dates of intrusion are as follows: 09/06/2021, 09/07/2021, 09/08/2021, 09/09/2021, 09/10/2021, 09/11/2021, 11/07/2021.
There is an importance of the dates. They were registered when all the customers using the web hosts were sent notified about the data breaches that matched with the security intrusion dates.
A customer that has been loyal to the breached web hosts is now facing problems on a regular basis. Their data are always under attack and the eyes of hackers. Some of the customers have also faced distortion of data saved that lead them into trouble.
Additionally, with the data breach, hackers are now enjoying the extra time to backdoors besides adding false administrative accounts upload scripts that are subject to danger. Technicians are failing to ensure a deadline to fix the issue.
The following is a part of the email sent to the customers of MediaTemple, “…we have determined that, on or about September 6, 2021, an unauthorized third party gained access to certain authentication information for administrative services, specifically, the customer number and email address associated with your account; your WordPress Admin login set at inception; and your sFTP and database usernames and passwords.”
-

 Domains5 years ago
Domains5 years ago8 best domain flipping platforms
-

 Business5 years ago
Business5 years ago8 Best Digital Marketing Books to Read in 2020
-

 How To's6 years ago
How To's6 years agoHow to register for Amazon Affiliate program
-
 How To's6 years ago
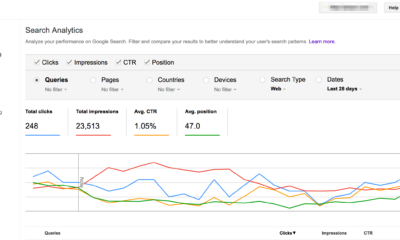
How To's6 years agoHow to submit your website’s sitemap to Google Search Console
-

 Domains4 years ago
Domains4 years agoNew 18 end user domain name sales have taken place
-

 Business5 years ago
Business5 years agoBest Work From Home Business Ideas
-

 How To's5 years ago
How To's5 years ago3 Best Strategies to Increase Your Profits With Google Ads
-

 Domains4 years ago
Domains4 years agoCrypto companies continue their venture to buy domains